Understanding the AWS zone of trust

Spend enough time in the official AWS documentation you will probably come across the phrase zone of trust. Even though it doesn't feature prominently, it's an important concept that I wish was covered earlier and in more detail. Knowing how to use the zone of trust to control access to your resources and write your policies will make you more secure on AWS, and help you take care of your part of the shared responsibility model.
Definition
The zone of trust is the implicit security boundary of your AWS resources.
By using this security model, AWS can (and does) say that you resources are "secure by default".
Principals such as IAM users and roles can access resources in their zone of trust of if they have an identity policy that grants them permission to do so. Princiapls outside the resource's zone of trust require explicit permissions from the resource's resource policy (in addition to their own identity policy), as shown in the diagram below.
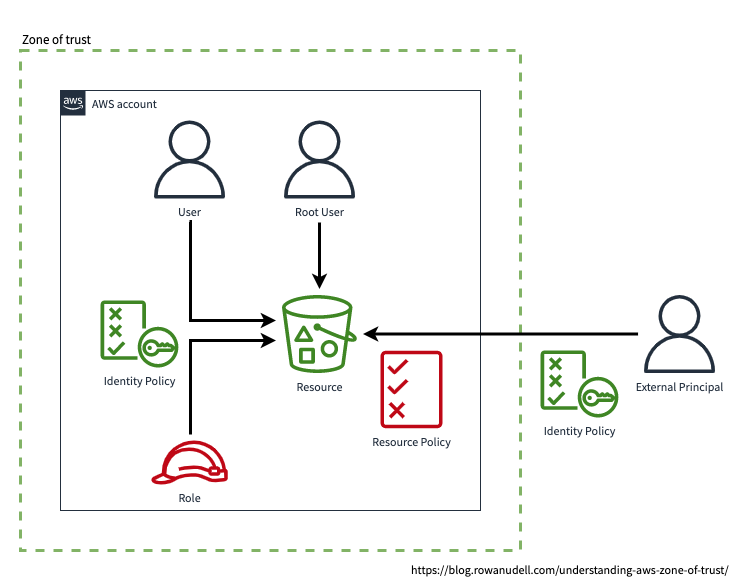
The AWS account root user is special case, because it has implicit access all resources in its zone of trust. As shown in the diagram, it doesn't require (nor can it have) an identity policy.
This example shows an S3 bucket, but not all AWS resources support resource policies. See the "Resource-based policies" column in the AWS services that work with IAM page for the services that you can share outside their zone directly.
To access resources that don't support resource policies from outside their zone of trust, you need to use cross-account role assumption so that you gain access to a principal in the resource's zone. I talk about this in greater detail in my book about IAM, and this approach works for all resources because the IAM role you assume is a resource that supports resource policies!
What about AWS IAM Access Analyzer?
A relatively new service, AWS IAM Access Analyzer is an IAM sub-service that reports on what principals have access to what resources. It has a nice feature that allows you to specify your AWS organization as a zone of trust, just keep in mind that this doesn't change the zone of trust for your resources or principals, only how this access is reported. By setting the organziation as the zone of trust, resources that are shared outside their zone, but within the organization will not be flagged as shared externally.