This question on re:Post shows a pretty sensible looking AWS IAM policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "ec2:DescribeInstances",
"Resource": "*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/aws:eks:cluster-name": "CLUSTER_NAME"
}
}
}
]
}
Only allowing ec2:DescribeInstances (which is required for the DescribeInstances API call) on a subset of EC2 instances is a good idea: you can ensure that users or services only have access to the specific AWS resources they should have, rather than all the EC2 instances in your account. Defining the subset via a tag on the resource also seems like a sensible thing to do too 👍
As the answer on the question points out, that IAM action doesn't support that condition. There's no issue with the actual StringEquals condition itself, which is what the author thought. There are a lot of conditions that I think should be supported by the relevant IAM actions, that aren't ☹️
The Service Authorization Reference documentation will tell you what service (in this case EC2) conditions are available, but only by looking at all the specific IAM action(s) for that service will show you the conditions supported by the actions:
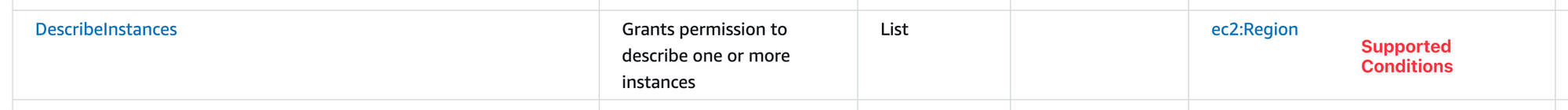
Unfortunately in this case there's no happy ending: until AWS adds support for that condition to that action, it won't work.